Course Description:
The Advanced SS7 Exploitation and Network Hijacking Techniques course delves into the intricacies of SS7 signaling in GSM and cellular wireless networks. Participants will learn about vulnerabilities, attack methods, and tools used to manipulate SS7 protocols. This course provides practical demonstrations and tutorials on installation, configuration, and exploitation techniques.
Course Content:
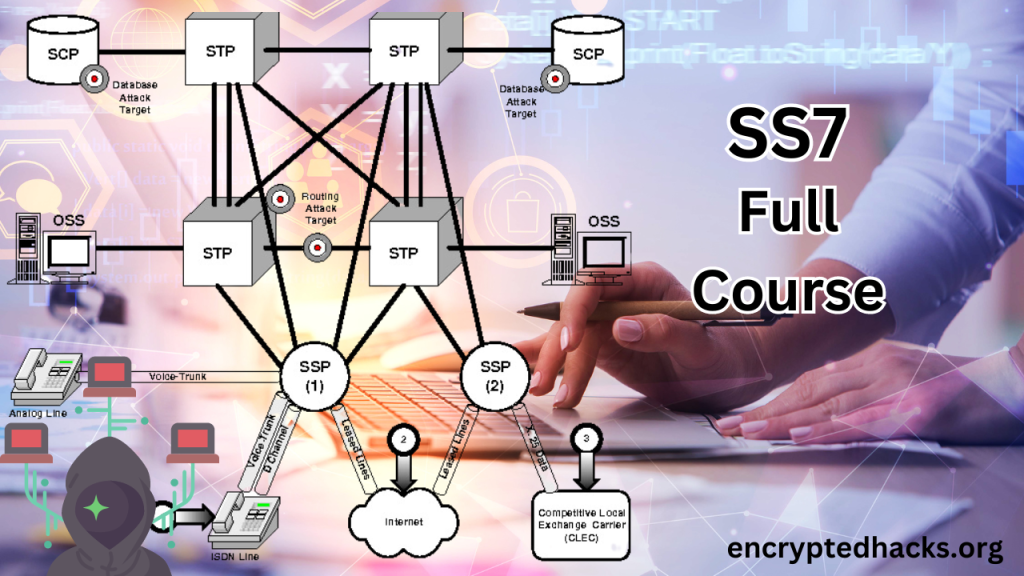
1. Hijacking Network Elements Over SS7 – A New Type of Attack
Exploring a novel attack vector for manipulating network elements over SS7 signaling.
2. Understanding Signaling SS7 in GSM & Cellular Wireless Networks
In-depth explanation of the significance of SS7 signaling in GSM and cellular networks.
3. Software & Hardware Requirements for SS7
Identifying the necessary software and hardware components for conducting SS7 attacks.
4. Installing HackRF in Windows 10
Step-by-step guide to installing HackRF on the Windows 10 platform.
5. Resolving SS7 Vulnerabilities in Kali Linux 2019.4 – Part 1
Techniques for identifying and addressing vulnerabilities in SS7 signaling.
6. SS7 Attack – Part 2 Kali Linux
Continuing the exploration of SS7 attacks in Kali Linux.
7. SS7 – Part 3: Cell Phone Signal Jammer in Kali Linux
Demonstrating the use of a cell phone signal jammer in conjunction with SS7 attacks.
8. C7 SS7 Osmo-BB in BackBox Linux 2020
Introduction to using C7 SS7 Osmo-BB in BackBox Linux for SS7 manipulation.
9. SS7 Global Access File in Kali Linux 2020.1
Utilizing the SS7 global access file in Kali Linux for advanced attacks.
10. SS7 GSM Sniffing with Wireshark – 100% Verified
- Demonstrating GSM sniffing using Wireshark for accurate and reliable results.
11. Installing SS7 and GSM Arsenal in Kali Linux
- Comprehensive guide to setting up SS7 and GSM tools in Kali Linux.
12. Implementing SS7 in Kali Linux
- Hands-on tutorials for implementing SS7 attacks within the Kali Linux environment.
13. SS7 Dependency Installation in Kali Linux 2020.2
- Ensuring all dependencies are correctly installed for SS7 attack methods in Kali Linux.
14. Utilizing SS7 Attacks for Stealing Facebook Logins
- Demonstrating how SS7 attacks can be leveraged for unauthorized access to Facebook accounts.
15. Capturing Voice Using GSM BTS USRP1 and Mobile Phones in Linux
- Practical guide to capturing voice transmissions using GSM BTS USRP1 and mobile phones in a Linux environment.
Note:
This course is designed for individuals interested in advanced SS7 exploitation techniques. Emphasis is placed on ethical hacking practices, responsible use, and compliance with legal frameworks. Participants will gain a deep understanding of SS7 signaling and the tools and techniques used to manipulate it.
0 Comments